Charting the progress of Australia’s electricity grid presents a paradox. On the one hand, we lead the world on consumer solar generation: 30% of people now live in houses with rooftop solar, with power generation totalling 9 GW (and forecast to reach 30 GW by 2030 (1)). On the other hand, regulation and the adoption of technology to facilitate the creation of a smart grid has been slow.
Recognising this, the Australian Energy Market Operator (AEMO) in December unveiled a new, ambitious infrastructure plan to empower the country to generate 25% of all its energy from home-based renewables. AEMO forecasting suggests that by 2050, half of all households and businesses will have solar PV installed, supported by networks of new storage technologies (including personal household batteries) and smart aggregators.(2)
While the benefits of distributed solar networks are well established, the increasing integration of grids with connected devices and future technologies, such as electric vehicles, also greatly expands the opportunities for cybercriminals to enter systems, access data and manipulate Australia’s national infrastructure. A successful cyberattack on operational technology within the solar grid therefore presents a core risk to safety, reliability and business continuity.
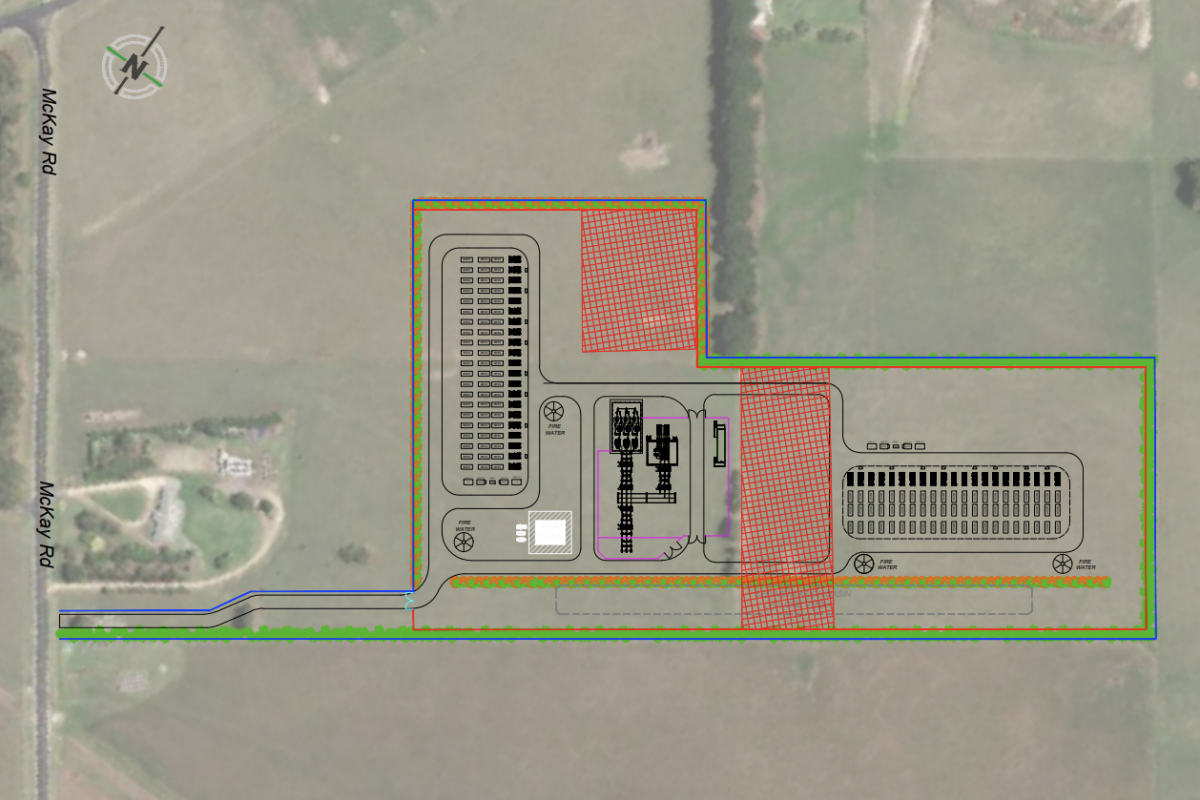
As Australia makes this bold transition, network visibility, security and control must be achieved from the grid level all the way to the bay level and to each individual intelligent electronic device (IED). Improving smart grid inter-connectivity, leveraging modern TCP/IP-based standards such as IEC-61850 and IEC-60870-5-104, and employing new techniques of data acquisition are becoming de facto industry standards.
I believe there are six cyber-based changes that Australia’s energy industry needs to prepare for as the distributed solar generation becomes the norm, rather than the exception:
1. IT/OT convergence will open up new attack vectors. The convergence of IT, OT and IoT is a key feature of smart grids, and the boundaries between them will continue to dissolve as Australian households adopt solar. This new reality will result in an expanding attack surface and vectors that need to be monitored and defended.
Energy technology leaders must therefore recognise that whether or not systems are air gapped, OT-based attacks present a real and present danger. The “set-and-forget” mantra is no longer the way to administer OT environments. Early detection of OT threats requires continuous ICS-specific monitoring capabilities at the network and device level.
2. OT-to-IT attacks will become a reality. While lateral attacks that gain a foothold in IT and spread to OT networks have been a well-documented concern over the past 24 months, OT-to-IT attacks will soon emerge. This means we can expect attacks to deliberately compromise OT networks in order to gain access to IT networks, which could potentially include data about households, and sensitive customer databases.
To counter this threat, an ecosystem of trust and cooperation needs to be created between IT and OT security for information sharing in order to detect these attacks. This must permeate down to the device level in order to stop attacks before they spread across the network.
3. IT teams must take ownership of OT security. Energy security must be a shared responsibility between OT and IT teams. IT teams will be tasked to take ownership for OT security since they have decades of experience with internet-connected applications and technologies. Although OT teams have traditionally objected to any IT intervention in ICS networks, this will change with the growing awareness of internal and external security threats. I expect IT teams to set guidelines for OT security projects based on requirements provided by OT teams, with best practice adopted from both fields.
Implementation of the UN-endorsed ISA/IEC 62443 cybersecurity standards will be an essential first step. These standards are the only consensus-based cybersecurity standard for automation and control system applications. By using these globally approved standards to increase productivity, lower costs and keep people, industrial facilities and commercial buildings safe, IT teams can bridge the gap with OT.
4. ICS-as-a-Service will gain acceptance. The cloud is the only reliable means to deliver OT security to remote solar-generation facilities where physical deployment is not practical. Leveraging the power of the cloud can yield certain benefits when it comes to securing your grid environment, including the ability to share anonymised data with other OT environments in order to find attacks earlier and close the vulnerability window. The cloud also enables security to be delivered to the plethora of microgrids needed to connect households and businesses to make distributed generation a reality.
5. The edge becomes more vulnerable than the core. Attackers will target less well-defended OT infrastructures, such as smaller substations or transfer locations at large grid environments. Typically, remote/smaller sites are connected to the larger OT network and, in the case of energy providers, to regional grids. As a result, a compromise at a remote site or a small energy provider could have cascading effects if an attack is able to spread, particularly if attackers are able to access sensitive information housed in localised microgrids.
Deployment of OT security via the cloud should be used to blanket not only core locations but also distributed systems that currently lack the same controls as primary installations.
6. The cyber skills gap will spread to OT. The global OT-IT skills gap puts Australia’s move to a smart solar generation at risk. Private and public organisations must map their skills gaps and then begin cross-training programs targeted to address each of the gaps. New talent must be recruited from universities to address security for the combined IT/OT footprint.
Cybersecurity is now widely recognised as a core risk to power networks the world over. To mitigate that risk, Australian operators and vendors connected to the grid must have full visibility, security and control of all operational assets, including IEDs, RTUs PLCs, breakers, meters, drivers and other devices. Otherwise, attacks could severely hinder rollout and negate the benefits of distributed solar generation and smart aggregation.
(1) Morgan Stanley, Consumer revolution: Shining a light on how the Utilities world is changing, https://www.morganstanley.com/ideas/consumer-generated-electricity
(2) AEMO Open Energy Networks Interim Report: https://aemo.com.au/-/media/files/electricity/nem/der/2019/oen/interim-report.pdf?la=en&hash=106DB3642BAEEBC37DA91614A57090B1
The views and opinions expressed in this article are the author’s own, and do not necessarily reflect those held by pv magazine.
This content is protected by copyright and may not be reused. If you want to cooperate with us and would like to reuse some of our content, please contact: editors@pv-magazine.com.






A bit unfortunate that this article helpfully explains the abbreviation for AEMO, but then leaves readers puzzled that this standard convention is not followed with other abbreviations, including those in the heading of the main point.
Could be a great article, but a percentage who might otherwise have read the piece will abandon without forming an opinion. And will remain still in the dark about items such as: OT, IT, ICS, IEDs, RTUs and PLCs.
If authors, and editors, are interested to win new readers, it can be helpful to bear in mind that not all readers start from where you are …
Hi to every one, the contents existing at this site are in fact remarkable
for people experience, well, keep up the goood work fellows.
A recent event in a remote natural gas pumping station, was shut down for two days when a cyber attack spear phishing attack got into the IT communications and “pierced” the OT communications where it completed a ransomware attack that took down the system. Once realized, it took the Gas companies technicians two days to take down the controlling servers, rid them of infections, reload the operating software back on and put the system back online. The so called, “onion approach” to data streams and information security ‘levels’, just makes the communications more difficult to monitor and correct attacks. Apparently there are those ‘out there’ that can peel an onion as easily as they can breach supposed hardware or firmware firewalls between system communications boundaries. The ‘only thing’ that may have saved this particular site from disaster is the SCADA protocol was basically shut down by the OT denial of service due to the spear phishing intrusion. This tells me, the Internet Technology, Internet of Things and the “boundaries” created by hardware, firmware are not adequate security functions. When one hole is “patched”, this may cause or create another hole to climb through. All of these layers of security is necessary and yet once someone learns to hack the security, it takes lots of manhours to find, determine, secure and fix the intrusion.
The CRC or cyclical redundancy check was probably the last line of defense from the SCADA system that allowed the gas pumping station to run as you were or shutdown with denial of service events.