Attacks on energy infrastructure in Ukraine and rising geopolitical tensions have brought energy security to the fore internationally. Meanwhile, the digitalisation of our lives and energy systems is shifting the foundations of what it means to be ‘secure.’
Since centralised energy infrastructure has been the main target of attacks to date, this segment has received the most attention around questions of security. Few of the cybersecurity frameworks that Australia has in place today extend to technologies like rooftop solar and other distributed energy resources. “With any emerging technology and its widespread adoption, fast paced innovation cycles create cybersecurity risks,” Professor Helge Janicke, Research Director at Australia’s Cyber Security Cooperative Research Centre told pv magazine Australia.
For the first time, households are generating and managing energy, using technologies that are marketed and made to be affordable to them – technologies which involve copious hardware and software components from different manufacturers, mostly foreign-owned, and have far looser grid connection standards than their large-scale counterparts.
“Centralised infrastructure is probably… going to have a system that is a lot more robust than an unregulated, commercially-interested company that is doing what they can to break into a market,” Grace Young, Chief Innovation Officer of clean-tech device company Wattwatchers told pv magazine Australia. “While that centralised infrastructure might immediately seem like honey pot, it quite potentially is much easier for somebody to get wide-scale control via a rouge piece of DER hardware or software.”
This isn’t cause for panic, but requires consideration. “We don’t want to sleep walk into something here,” Sunwiz founder and managing director, Wawrick Johnston told pv magazine Australia.
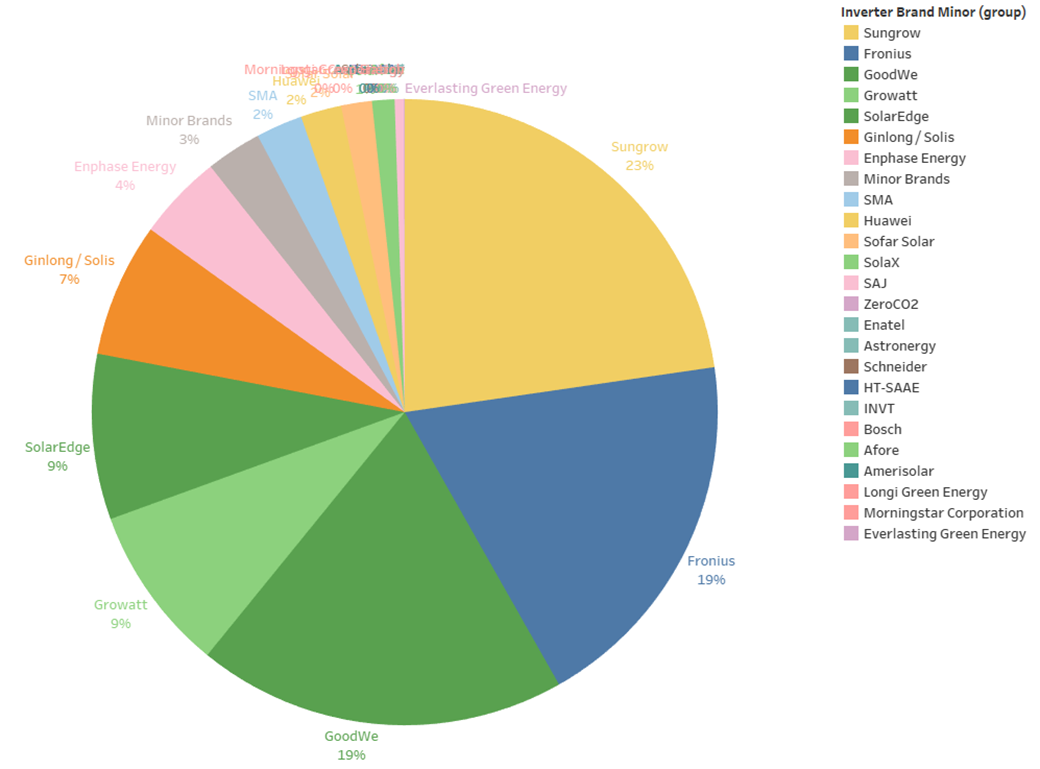
Image: Sunwiz
Before we go into particularities DER technologies, it’s worth doing a brief overview of what’s been happening in the nation’s energy cybersecurity space.
A brief overview of Australia’s energy cybersecurity landscape
In December 2022, Australia’s Minister for Cyber Security, Clare O’Neil, announced the development of the 2023-2030 Australian Cyber Security Strategy. An expert advisory board will help develop the strategy, with the government only closing public submissions in April.
This is not the Commonwealth’s first foray into addressing the issues that come with moving the national energy system from thermal generation to inverter-based technologies. In 2018, Australia introduced the Security of Critical Infrastructure, or SoCI, Act. The legislation imposes cybersecurity obligations on critical infrastructure owners, including electricity, gas, and liquid fuel asset owners as well as energy market operators. To be subject to the policy, generators must have an installed capacity of at least 30 MW and be connected to the national energy market.

Image: Clare O'Neil/LinkedIn
While these standards don’t capture DER technologies at the moment, Professor Janicke says there is a significant national effort looking at the security of Distributed and Consumer Energy Resources (CER). The Cyber Security Cooperative Research Centre (CSCRC), he noted, is funding a test laboratory where systemic risks are explored.
“The CSCRC is also leading a national working group on cybersecurity bringing together key stakeholders in Australia’s energy ecosystem, contributing to other national initiatives around CER security,” Professor Janicke said.
There are also international efforts to tackle this issue, with Smart Energy Council CEO, John Grimes, pointing to revisions of the ‘IEEE 1547.3 Guide for Cybersecurity of DERs Interconnected With Electric Power Systems’ being led by US agency NREL. “Manufacturers around the world are also heavily involved in the establishment of global cybersecurity standards for DER & other renewables,” Grimes told pv magazine Australia.
Emerging standards on Internet of Things (IoT) device security and the European Cyber Resilience Act (CRA) will benefit Australia too, Professor Janicke noted.
Finally, the Australian Energy Market Operator (AEMO) has been collaborating with industry and government to develop a tailored cybersecurity framework for Australia’s energy sector, known as the Australian Energy Sector Cyber Security Framework (AESCSF).
While it seems this voluntary program has so far focussed more on larger-players in the energy market, the 2023 program points to a focus on “less cyber mature energy organisations,” which AEMO notes “are unlikely to be captured by the SoCI Act but play an increasingly important role in maintaining energy security.” AEMO’s AESCSF team did not respond to requests for comment, but this sentiment would appear to signal towards heightened attention on the DER space.
All this is to say, risks are not being disregarded. Since the work being done around cybersecurity is largely ongoing, it is difficult to say exactly where the parameters for any upcoming standards will fall though.
There are at least three distinct fields of risk which experts have flagged, all of which receive quite different amounts of scrutiny.
Those are the communication channels DER devices use, their internal security programming, and the device’s supply chain.
The supply chain question
While DER systems include various technologies, inverters are a key focus because they are the point where the home and national grid connect. The role of inverters is also shifting as the penetration of DER grows, with the devices increasingly being used for control. From next month, July, the inverters of new solar systems in South Australia will be required to have software capable of “dynamic exports” – that is, the inverters will receive instructions based on network conditions and will adjust system output accordingly. More on the implications of this increasingly popular program in part two, but suffice to say inverters are key.
To date, many of the discussions around cybersecurity in the DER space have raised or alluded to popular Chinese equipment manufacturer Huawei, with the company’s ties to the Chinese government frequently noted. This is a touchy subject, and hard to disentangle from broader anti-Chinese sentiment which politicians often play on.
Whether or not a single company being the focus of so much attention is warranted, equipment origination certainly mounts security questions. In a report on the cybersecurity findings from DER marketplace demonstration Project EDGE, AEMO noted: “Each entity across the DER Marketplace would have their own supply chains based on their business requirements. Such supply chains provide a threat actor with opportunities to perform malicious activities targeting a specific DER Marketplace entity. For example, a misconfigured device, or backdoor enabled software application.”
AEMO notes such risks could be mitigated by introducing cybersecurity requirements for key suppliers “according to industry better practices” and says “information sources should be monitored.” It adds these key suppliers should have appropriate Third Party Risk Management (TPRM) processes, which would enhance the visibility of risks and control.
Of the three risk fields, this is probably the most conceptual in that it exists today mostly as a hypothesis. However, as Professor Janicke notes, the threat posed by supply chains is a crucial consideration as it could give rise to “systematic” issues.
Connection security & the problem of wi-fi
Unlike large-scale projects, most DER devices depend on household wi-fi, public internet connections or are monitored through cloud services on your mobile phone.
“Those communication channels are not secure and there’s a lot of potential along the way for things to be intercepted,” Wattwatcher’s Grace Young said. “That can then present therefore a flow on security risk down the path because if a slack [device] developer accidentally exposes secrets within a communication within an insecure channel that can open up the broader infrastructure to issues,” she added.

By secrets, Young is referring to passwords, API keys, etc. Interestingly, just this week the US’ Cyber and Infrastructure Security Agency (CISA) flagged a version of Enphase’s Envoy communication gateway as having this issue. “Enphase Envoy versions D7.0.88 and prior are vulnerable to a command injection exploit that may allow an attacker to execute root commands,” CISA announced, with Solarquotes reporting the device’s software was discovered to have “hardcoded credentials” – that is, user name and password are written into the software.
Young noted that if communication channels aren’t secure or expose secrets, it increases the “attack surface,” meaning how big potential entry points into the system are.
“My understanding of the standards that are currently under development, and notably the international 2030.5 and its ‘Australianised’ version known as CSIP-AUS [Common Smart Inverter Profile Australia], is that they aren’t intended to look at the security of the underlying infrastructure. They are really just standards on the interoperability of these systems to respond to system commands,” Young said.
“There’s kind of an underlying assumption that these devices are communicating securely…and that assumption may not return true,” she added.
Again, in its Project EDGE report, AEMO noted DER devices’ reliance on public communication channels concerning.
Internal device security
Another key, undiscussed consideration is the actual security of end devices.
The level of cybersecurity designed into devices is largely left to manufacturers. Some companies, including Wattwatchers, take cybersecurity very seriously, but it is understood the level of readiness within industry devices is fairly varied.
“If you’re not really focussed on it, there’s a lot more area where things can go wrong,” Young said. Programming watertight systems or, as it is often referred to, ‘security by design’ is obviously a far more onerous undertaking, and companies may simply be more focussed on their path to market especially in those early stages.
‘Proof of concept’ programs get used in production “way more that anyone wants to admit,” Young noted. Device developers may take shortcuts when writing these programs because they are intended only for demonstration. “Then suddenly you’ve got a compromised device in the field and then suddenly you’ve got a compromised device in the whole system,” Young said – again creating hackable openings.
In the Project EDGE report, AEMO deems vulnerabilities in DER marketplace software, firmware, third-party applications, as a ‘critical’ threat. “Given the nature of the distributed environment, weaknesses in the software/applications could have serious implications which could affect the DER marketplace as a whole,” the report noted.
“These are the sorts of challenges I think we need to be considering, especially when we are talking about control devices,” Young said.
In part two, pv magazine Australia looks at the potential consequences should vulnerabilities be weaponised.
–
Grace Young will present the talk ‘A real-time marketplace for energy data: How do we strike a workable balance between open, proprietary, industry, customer, private and secure?‘ at EnergyNext in Sydney on July 19, 2023.
This content is protected by copyright and may not be reused. If you want to cooperate with us and would like to reuse some of our content, please contact: editors@pv-magazine.com.









1 comment
By submitting this form you agree to pv magazine using your data for the purposes of publishing your comment.
Your personal data will only be disclosed or otherwise transmitted to third parties for the purposes of spam filtering or if this is necessary for technical maintenance of the website. Any other transfer to third parties will not take place unless this is justified on the basis of applicable data protection regulations or if pv magazine is legally obliged to do so.
You may revoke this consent at any time with effect for the future, in which case your personal data will be deleted immediately. Otherwise, your data will be deleted if pv magazine has processed your request or the purpose of data storage is fulfilled.
Further information on data privacy can be found in our Data Protection Policy.